Do you want to target software vulnerability and deny a user from accessing a network or website? These 12 best DDoS Attack Tools help you flood any computer network with queries, requests, and packets effortlessly.
Denial of Service (DoS) is an attack tool typically used to restrict authorized users access to a resource like accessing emails, networks, websites, etc. On the other hand, DDoS (Distributed Denial of Service) is a form of DoS attack that involves several compromised machines that target the same victim. The DDoS uses data packets to flood the computer network.
DDoS has various attack tools it uses to create an attack against any targeted server. The following is a curated list of DDoS Attack Tools you can use to mount an attack against any network, websites, computer, etc.
Navigation of Contents
1. HULK (HTTP Unbearable Load King)
HULK is a web server Dos attack tool. It is typically created to help bypass system cache engines and generate obscure traffic.
Features of HULK:
- Hulk helps generate a high traffic volume at the webserver
- It can also generate obscure and unique traffic
- It helps bypass system cache engine
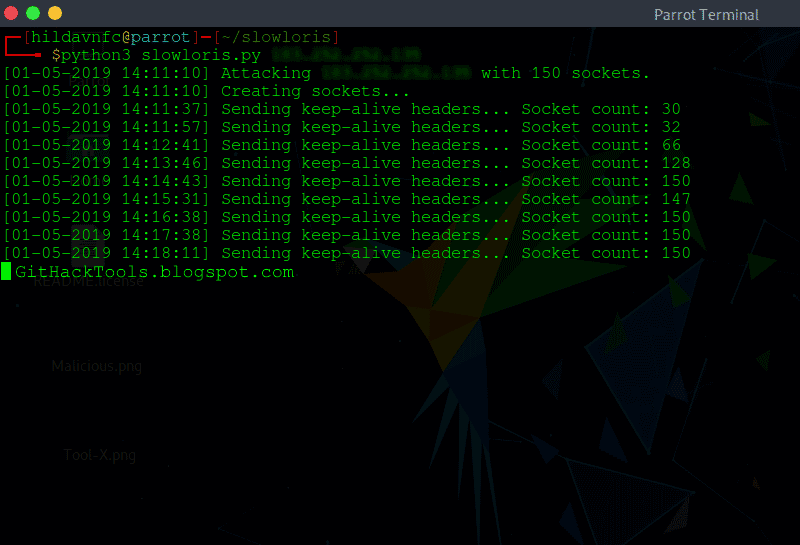
2. Slowloris
Slowloris is a DDoS attack tool that you can use to attack a server by making it down.
Features of Slowloris:
- Slowloris ensures to hold the connection for as long as it can
- Slowloris attacking tool helps engage the maximum connection with the open ones
- It floods the server with an authorized HTTP
- Slowloris does not affect other ports and services on the target network
- It denies request to the legal connections by overflowing the connection pool while it keeps the false connection open
3. Xoic
Xoic is a DDoS attack tool that helps you carry out an attack on smaller websites. It uses TCP, UDP messages to carry out its attack.
Features of Xoic:
- Xoic is simple to use
- It offers three attacking modes
- It has a testing mode and a normal Dos attack mode
- It attacks Dos with ICMP, UDP, HTTP, or TCP message
4. LOIC
Also known as Low Orbit ION Cannon, LOIC is an open-source tool that can be used to carry out a DDoS attack. It is often written in C# and transmits UDP, TCP, and HTTP requests to the server.
Features of LOIC:
- LOIC carries out stress testing to verify the system's stability
- It doesn't hide an IP address whether the proxy server is working or not
- LOIC also helps you to carry out an online DDoS attack against any of the websites they control.
- It is one of the best free DDoS attack tools that enable you to the network performance
- You can use LOIC for DDoS program identification. It identifies any DDoS program that hackers might use to attack a computer network
5. SolarWinds Security Event Manager (SEM)
SolarWinds offers an effective prevention and mitigation software known as Security Event Manager (SEM). SEM is used to prevent DDoS attacks. It does this by tracking event logs from various sources for spotting and preventing DDoS malicious activities.
Security Event Manager (SEM) helps control servers and identify potential command interactions by taking control over community-sourced list of malicious acts. Owing to this, it reviews, normalizes, and consolidates logs from different sources such as servers, firewalls, IPS/IDS, etc.
Features of SolarWinds:
- SolarWinds helps you design filters according to parameter combinations, IPs?accounts, or specific timeframes.
- SolarWinds' method of maintaining events and logs makes it a source of truth for DDoS mitigation and post-breach investigation.
- SEM also stores the events and logs in a compressed and encrypted pattern and record them in an unchangeable read-only format
- SEM enables you to set up the options by making use of checkboxes
- It also has various functionalities of automated responses such as shutting down an account, blocking an IP, or sending alerts.
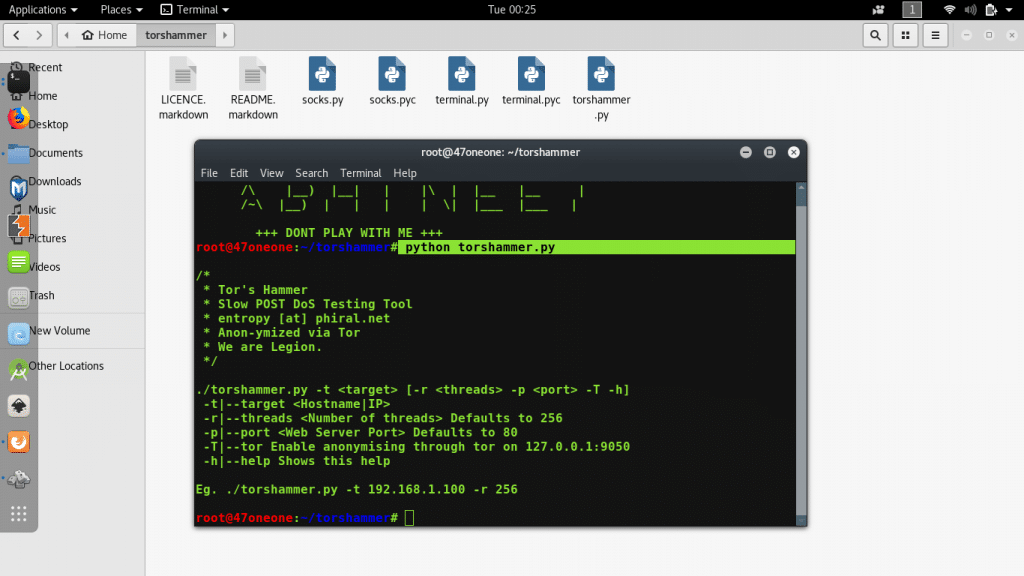
6. Tor's Hammer
Tor's Hammer is a DDoS attack tool that also functions as an app-layer DDoS software program. It is useful for targeting web servers and web apps. Tor's Hammer carries out a browser-based internet request performance that is used for loading web pages.
Features of Tor's Hammer:
- Tor's Hammers enables you to quickly link various artifacts in your project
- It uses web server resources by generating various network connections
- It converts URL into links automatically
- It can keep connections and HTTP POST requests for one thousand to three thousand seconds
- Tor's Hammer also enables you to create rich text markup by making use of a plain text formatting syntax tool called ‘Markdown'
7. DDOSIM
DDoSIM is also known as DDoS Simulator. It is a DDoS attack tool that is used to create a complete TCP connection. The tool is also useful for carrying out a DDoS attack against a target server. It has a C++ language and can be used on platforms such as Linux.
Features of DDOSIM:
- DDOSIM enables you to flood TCP connections on a random network port
- It offers various options to carry out a network attack
- DDOSIM also helps you target a server by creating complete TCP connections
- It displays a server's capacity to handle app-specific DDoS attack
8. PyLoris
PyLoris helps to test the vulnerability of a network. It does this by carrying out an online DDoS attack. It is useful for controlling badly managed reoccurring connections and also for managing DDoS online.
Features of PyLoris:
- PyLoris supports Linux, Mac OS, and Windows
- It can be run using Python script
- PyLoris has the newest codebase (a source code collection for building a specific software system)
- It carries out network attack by using HTTP request headers
- It offers an easy-to-use Graphic User Interface (GUI)
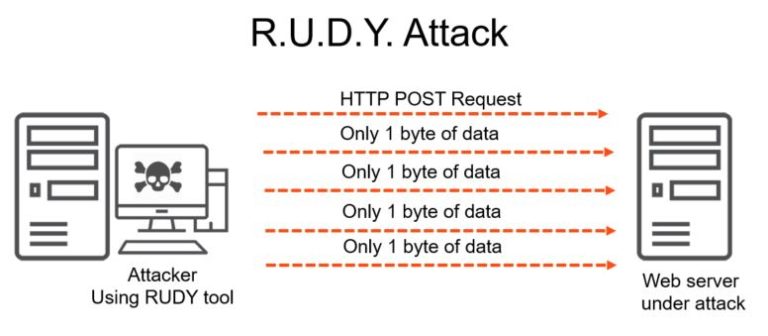
9. RUDY
RUDY is a DDoS attack tool that enables you to easily carry out a DDoS attack online. RUDY is an acronym for R-U-Dead-Yet. It helps you target cloud apps. It does this by starving available sessions on the webserver.
Features of RUDY:
- RUDY has an easy and simple tool
- Its console menu is often interactive
- RUDY instantly browses the DDoS target website and spot embedded web forms
- It helps you to carry out HTTP DDoS attack by making use of long-form field submission
- It instantly detects form fields for data submission
10. GoldenEye
GoldenEye attack tool carries out its DDoS attack by sending an HTTP request to the target server. It uses cache-control options paired with KeepAlive message to carry out socket connection busting.
Features of GoldenEye:
- To get mixed traffic, GoldenEye randomizes POST, GET, etc.
- GoldenEye arbitrarily creates user agents
- It has an easy-to-use application written in Python
- GoldenEye absorbs all the HTTP/HTTPS sockets on its app server to carry out a DDoS attack
11. DAVOSET
DAVOSET is a DDoS attack tool. It is also a software used for performing a DDoS attack by abusing the functionality of any website. DAVOSET helps you carry out a DDoS attack without stress.
Features of DAVOSET:
- DAVOSET is one of the best DDoS attack tools that offer cookie support
- In performing its attack, DAVOSET offers a command-line interface
- It also enables you to perform an attack by making use of XML external entities
12. OWASP HTTP POST
OWASP is an acronym for Open Web Application Security Project. It helps you to perform a web application test to examine its network performance. OWASP also enables you to perform a DDoS from a single machine.
Features of OWAS HTTP POST:
- OWAS HTTP POST enables you to decide the server capacity
- It allows you to share the result under its license
- This attack tool can be used for commercial purposes
- It helps you carry out a test against the app layer attack
- OWAS HTTP POST lets you transmit and distribute the tool with others
Conclusion
In this article, we have examined the various tools for carrying out a DDoS attack. The list of tools discussed is the top best for performing a DDoS attack. The tools can also act as a unique resource for security and performance testing.
Lastly, XOIC and LOIC are very easy to use. LOIC is a DDoS attack tool that you can also use testing. HULK is also useful for research purposes. PyLoris and RUDY play a huge role in carrying out testing activities.